Never assume that your email security is adequate. Since the invention of the telephone, communication between individuals has advanced significantly. Letters, payphones, cordless calls, and electronic mail are just a few examples.
If you are finding yourself wondering what email breach security is, you have come to the right place.
Email is used by most firms, and they even rank among the most crucial channels for business communication. Its adaptability in conveying information from future events, clients, team memos, and a few more renders it a unique corporate weapon.
It could be inappropriate for anyone outside of the business and social group to access your personal space when there is so much data circulating through your emailing hub.
Sadly, it could be a reality. It’s possible that clicking that banned link under the influence of a con artist will create a hole in your system, sufficient for scammers to enter. And believe us when we say that data breaches are no simple matter.
Top 10 email security techniques to protect your business against data breaches in 2022
There are some systems that promise you an additional encryption layer to protect your emails even more, but greed serves as the killer app of cybercriminals and nosy rivals.
Be at ease, though, as there are solutions to this conundrum. We’ll be frank and suggest that these fundamental email security procedures can help safeguard your workspace from thousands of data breach dangers.
1. Understand if there has been a data breach
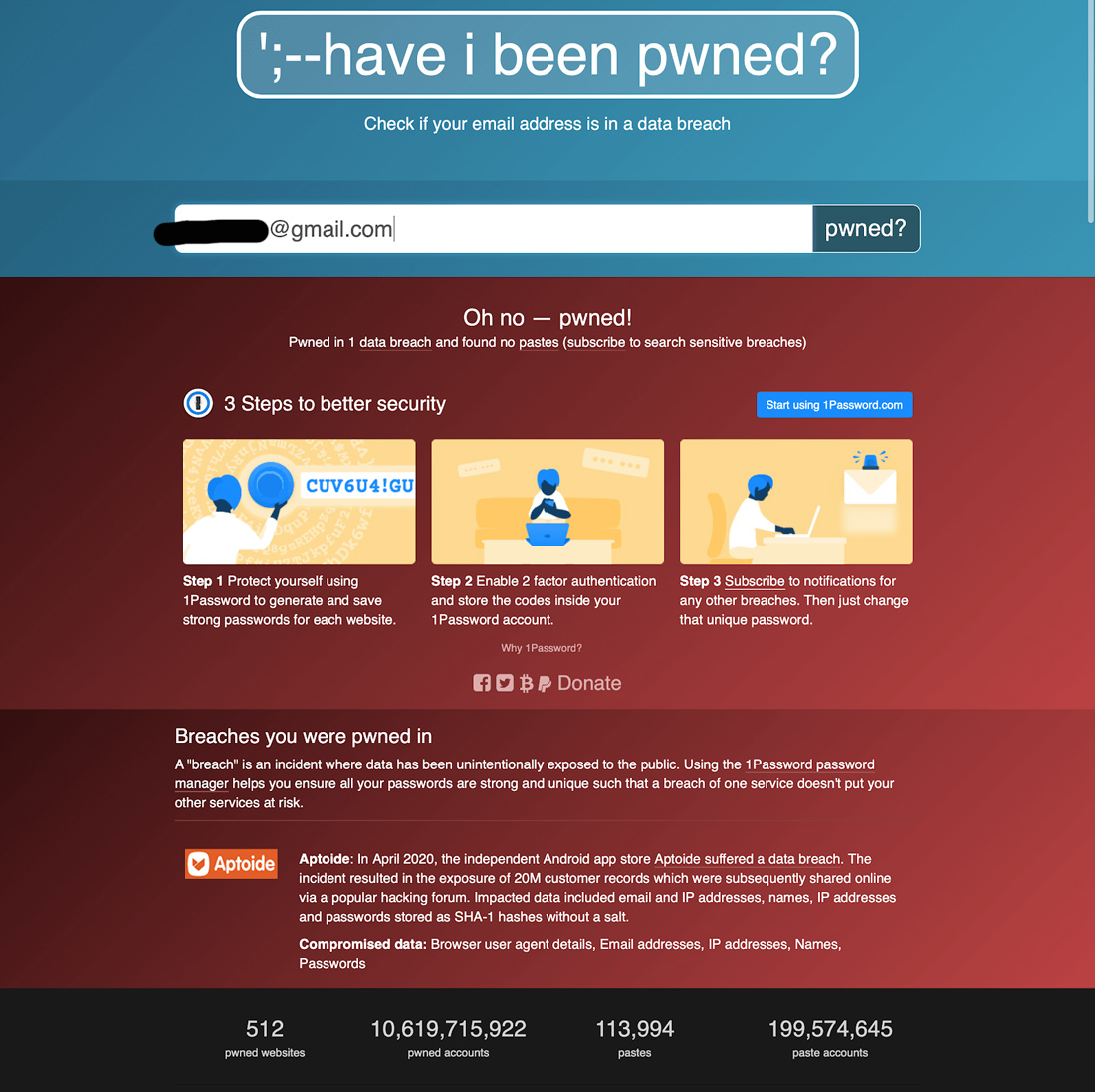
Finding out if a data breach has exposed your personal information is crucial. You can do this manually by reading the most recent data breach news.
If your email has been linked to a data breach, certain sites can show you that. You can quickly determine if your email has been exposed to any data breaches, which ones, and get further context on the leak. You can also read this guide for a step-by-step manual on how to increase your own security.
It’s important to note that an increasing number of businesses such as Firefox let you verify whether your personal information has been compromised right inside their application. In the event that your details have been exposed online, Google will also frequently send security emails.
2. Make your email password strong
How many individuals use the password “123456” will shock you. Either this or they submit “123456789” in full. Users should definitely talk about this since well over three million individuals use both of those passwords together.
Your private emails are at risk as well as the security of emails. Consider the fact that thieves focus much of their energy on picking locks rather than destroying your door. Even though it is theft, it’s the cleanest method of getting to your home.
Your password has the same function in the end. The simpler your passwords, the more probable it is that someone will hack into your account. Below are some strategies for managing passwords (some of which are recommended by the portals themselves):
- Use a combination of capital and small letters
- Add numeric and special characters
- Avoid sharing personal information like births, student identities, places of residence, or any other details
- Use phrases rather than words
3. Put two-factor authentication to use
Although it appears only a skilled computer user could complete the cybersecurity measure, it’s actually not that complicated. It essentially amounts to installing an additional lock on your door and another barrier to your profile. Fortunately, almost all email platforms allow two-factor authentication. However, if your present setup doesn’t already allow it, feel free to transition to some other email service.
In essence, even though a hacker is successful in guessing your “123456” password, he would be prevented by the two-factor verification, which requires him to submit a passcode before he is given access to your email. The most common ways to receive these credentials are email, SMS, voice calls, and apps that use time-based one-time passwords (TOTP).
4. Alternate your passwords as frequently as you can

You may well be accustomed to avoiding changing passwords since it is annoying to be forced to memorize them, but the business world is absolutely unforgiving. Changing your passwords frequently is among the easiest ways to ensure the safety of your email accounts.
Every year, data breaches and password leaks occur, and thieves often wait a specified amount of time prior to striking back. Consider your password to be your initial line of security, and you should change it at least once a year to strengthen your defense.
5. Keep an eye on daily email usage
This is similar to practicing your fundamentals. Even though it seems easy, doing this pays off in the long term. If you are a professional, you almost certainly use your work emails throughout your day. Today, it is essentially equally vital to drink and eat. You ought to preserve a record of your emailing activities with it. You can commence by being aware of:
- How many emails do you receive?
- How many emails and texts do you exchange per day?
- Do you invest the majority of the time reading email conversations from senders outside of the company?
Each of these concerns is directly related to risk considerations for the safety of your business emails, even though you may not give them much thought. There are multiple tools that can help you come up with concrete numbers by learning further about your behaviors and potential email security threats.
Read more: Using proxies for email protection
6. Check “phishing emails”
“Phishing emails,” among the various ways cybercriminals acquire your account credentials, are modeled after a fun outdoor pastime. Similar to fishing, such emails will lure you in by asking you to “sign-in” to your profile when in reality all you’re doing is giving them your email address, password, and sometimes other sensitive data.
Most phishing emails claim to be from one of your favorite service providers, like PayPal or your bank. You’re certain to lose corporate email security if you ignore the email’s address, voice tone, as well as, the language of the message.
7. Open attachments only after scanning them
It is imperative to emphasize this. Your business account is often used exclusively to receive and send work emails.
All you may be anticipating from a certain financial firm is a summary of a task. However, this isn’t always true since some emails can also arrive from unidentified senders and even include attachments that you can access.
You could be curious about this. Additionally, it could even be a legitimate email, so you cannot just dump it in the trash. To combat this issue, you can utilize email security solutions or strengthen email security procedures. Antivirus and/or anti-malware software, for instance, are technologies that let you scan such files.
At the bare minimum, you won’t hesitate to delete the email and even permanently block the person if these applications alert you that there appears to be an issue. The outlook? There was a good likelihood that a data breach would have occurred if you had accessed that file.
8. Never use public WiFi to access emails

Like shouting your social media passwords in a shopping center, this is a similar action. Public WiFi networks or even free web hosting providers are never secure, as you may already be aware. You could have just as easily welcomed the scammer into your system.
For these hackers to be aware of the type of data moving via that network, simply the most basic software is required. Encourage your friends and coworkers to utilize cellular data whenever they are away from the workplace to prevent this from occurring. It’s okay if it’s not as quick. Provided you are aware that it’s superior to free WiFi, you are set to proceed.
9. Use caution when using any equipment
A small number of businesses now support the bring your own device concept. As the name implies, this permits workers to use their individual computers and other personal devices for work-related purposes.
Yet, if your gadget isn’t configured with the proper email protection tools and procedures, this isn’t particularly useful. Just be cautious with your own technology. This includes refraining from logging into your personal and corporate email accounts on any gadget you come across. Now that certain gadgets may remember what you just entered, you should exercise caution when using public laptops and desktops.
10. Do not divulge your email address
Your professional email should not be accessible to all. As far as you can prevent it, try avoiding it given how many websites are now skulking around and requesting your email addresses. Always keep in mind that internal updates and newsletters will only ever be sent to your official email address.
But, others have gone above and beyond to subject you to even greater risks by selling your data to unaffiliated businesses. Although it’s not the most technologically advanced method, it represents a significant advancement for emails as a whole.
Conclusion
Finally, when finished, sign out of the email account. This is unquestionably a fantastic (and appropriate) way to conclude the list of the most effective email security standards. When you have completed all of your tasks and had a successful day, don’t neglect to congratulate yourself, but more significantly, sign from your email.
You could be using a strange device and neglect to sign out. While you’re about it, you might as well hand them the reins to your automobile as well. Generally, practice this even using your own device so that, if necessary, you are comfortable performing it on new gadgets.
Author bio

Atreyee Chowdhury works full-time as a Content Manager with a Fortune 1 retail giant. She is passionate about writing and helped many small and medium-scale businesses achieve their content marketing goals with her carefully crafted and compelling content. She loves to read, travel, and experiment with different cuisines in her free time. You can follow her on LinkedIn.
This article was submitted to us by a third-party writer. The views and opinions expressed in this article are those of the author and do not reflect the views and opinions of ThisHosting.Rocks. If you want to write for ThisHosting.Rocks, go here.